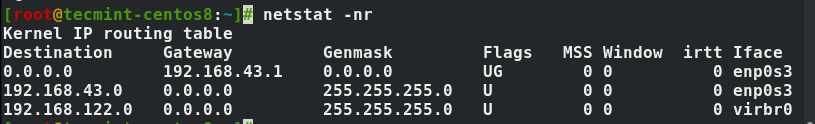
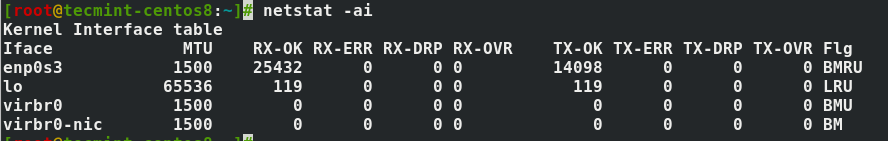
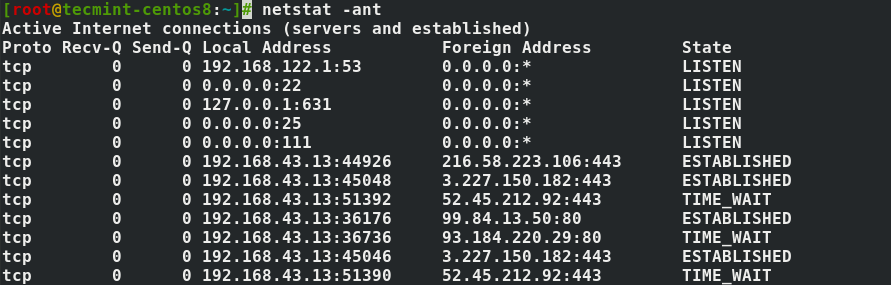
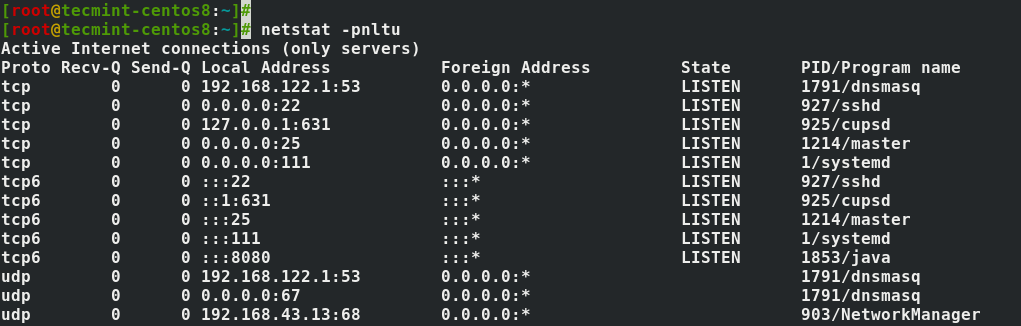
Phishing is one way that identity thieves, scammers and fraudsters steal information. They do this through the use of social engineering or deception. The goal is to trick you into divulging confidential or personal information which can then be used for fraudulent purposes, like identity theft.
They need to get enough information to impersonate or even replace you, in the virtual world of the internet or in a modern bank. This information can be as basic as your full legal name, social security number and home address. It can also get as in-depth as bank account numbers, online banking login credentials, your mother’s maiden name and can even include the secret questions and answers for your online banking or PayPal accounts.
The different types of Phishing
There are several different kinds of phishing that are aimed at different groups. The most common type of phishing is a simple email claiming to be from someone that plausibly needs information from you in order to accomplish something that is of benefit to you. There are claims of funds that need to be transferred to your bank account, fines that need to be paid to keep you out of jail, requests for tax and financial documents or just about anything else that would result in you sending the attacker whatever they are asking for. Apart from the general attacks, here are some more targeted variants of phishing attacks.
Spear Phishing
Spear Phishing is a targeted form of phishing. In a spear phishing attack the attacker has some information about you before they send you anything. They monitor your social media presence to see if you post anything about recent purchases. They keep an eye out for any mention of online retailers you’ve shopped at, products purchased online or even dating sites.
If you tweet that you just bought the newest iWatch from Best Buy, they have bait for their trap. Because they are already watching your social media presence, they know a bit about you, like your name and probably the city that you live in for starters.
They can then use their knowledge of you to craft an email claiming to be from Best Buy. This email may claim that there was a problem with your credit card for your recent purchase and that you need to fill out their online form to verify your card information. Or, they could claim to be a friend of yours wanting to know if you’ve installed this really cool app for your new iWatch. If not, they have a simple registration form ready for you to fill out to get the app. They might even pretend to be someone from the dating site claiming that your profile needs to be completed before you can get any more views.
The possibilities are virtually endless here and can, as we reported earlier this year, include blackmail.
Whaling, or CEO Phishing
Since the whole point to phishing is to gain unauthorized access to information, why not phish those who hold the keys to the most information. Attackers who target high level executives in corporations do so to gain access to the email account of someone in authority. With full access to that account they can gain access to any employee’s information, initiate fraudulent wire transfers or wreak havoc in just about any department of the company.
Not many people will double check to make sure the VP of sales really does need all of HR’s files on the entire sales team. Realistically, when was the last time you replied to a directive from your boss with “Really? Are you sure you need that?” It just doesn’t happen.
Related: CEO fraud and how to avoid it.
W2 Phishing
An even more targeted version of whaling is when an attacker uses or spoofs an executive’s email account just to get the W2s of employees, or the W9s of contractors. Tax season is the worst time for these kinds of attacks, as most company’s payroll departments are used to receiving these kinds of requests.
These requests don’t even need to come from a company executive. They can be spoofed so as to appear to come from the IRS, the maker of a certain brand of popular tax software or even from a CPA office. The most effective ones do appear to come from a high level executive inside the company, but appearing to come from the IRS can instill just enough fear to avoid scrutiny.
Phishing to deliver ransomware
In 2016 it is estimated that ninety percent of phishing emails carried some form of ransomware. While the goal of phishing is to gain access to information, the attackers are starting to bundle a ransomware package to up their income from these attacks.
The truly insidious part here is the belief amongst these attackers that anyone who is gullible enough to fall victim to phishing is also likely to pay the ransom when their files and photos have been locked up. Unfortunately, the statistics at the end of this article support this belief.
Vishing
With the rise in popularity of Voice over IP (VoIP) technologies, some phishers have taken to simply calling people to try to phish for their information. A VoIP server can be setup to mimic just about any entity that a phisher wants to impersonate, from a bank to a branch of the government. The sky really is the limit here.
The ability to change the caller ID information supplied by the server combined with the ability to select which area code the server is calling from make it child’s play for a scammer to pretend to be someone else over the phone. Factor in the amount of outsourcing these days and they don’t even have to have English as their first language to be marginally successful at this.
See also: What is vishing and how to avoid it.
SMiShing
According to a report from 2010, 90 percent of text messages are read within three minutes of receipt, and 99 percent of text messages are read. It’s no wonder that SMS messaging has become yet another vector for scammers to target victims.
Just like any other phishing campaign, the scammer sends out a bulk text message to hundreds or even thousands of phone numbers with claims like “Your credit/debit card has been deactivated due to suspicious activity. Please call our toll free number to verify your details.” or “You’ve been selected to win a $1,000 shopping spree. Simply be one of the first 100 visitors to this webpage to claim your prize.” Again, the tactics are aimed at getting a fast response and to collect as much information about the victim as possible.
Related: What is SMiShing and how can it be avoided.
What are the most common tactics for Phishing attacks?
The most common tactics employed are delivered via email, with the emails pretending to be from PayPal, one of the large banks, or even from the FBI, CIA or Department of Homeland Security, to name a few. The emails will contain all of the official looking logos for the entity being impersonated, but will contain two very important giveaways:
- There will be a strong sense of urgency requiring you to take action immediately to prevent something terrible from happening to you, like asset seizure, account lockout or even arrest
- They will either have an attached file that you need to fill out or a link to a website with fields of personal information for you to fill out
Keep in mind that the goal of a phisher is to collect information that you wouldn’t hand out to just anybody. To do that, they need you to think that you’re dealing with someone in authority and that they have a valid reason for collecting this information.
Examples:
- PayPal sent you an email saying that they have detected suspicious activity on your account. As a courtesy, they have locked your account until such time as you provide enough information to prove that you are the rightful owner of the account in question. The way you do this is either by filling out the attached form and clicking its “Submit” button or by replying to their email with answers to a list of questions, like “what is your mother’s maiden name?” and “what bank do you use for your personal checking?” and even “what are your bank account numbers for all of your current accounts?”
- Wells Fargo has noticed some suspicious activity with your credit card and have locked up your account. To unlock your funds, you will need to fill out the attached document and email it back to them using the link provided in the document
- The FBI has tracked illegal activity to your computer’s IP address. If you do not fill out the attached form and remit bail (usually one bitcoin) a warrant will be issued to your local law enforcement agency to apprehend you and hold you until your trial.
- You won a lottery which you never bought a ticket for.
Phishing websites are also an effective way to get unsuspecting users to submit information that they would normally not give out. These can be fake login pages designed to exactly resemble a popular or common company. According to Symantec, users of a popular cloud file storage service, Dropbox, were presented with a fake login page that was being hosted by the very same cloud file storage service.
A really complex version of this tactic is used to get the user’s login credentials, which are recorded by the fake login page in plain text for the attacker to use later. The user’s browser is then redirected to the real site’s login page with the submitted credentials. The overall effect is that the user is logged in without any sign that their information has just been stolen.
The attacker can then, at their leisure, log in to the user’s account and have their way with it. They can also test those same credentials against other online services to see if the user in question used the same username and password combination anywhere else, like Gmail, Yahoo!, eBay or all of the major online banking sites.
The internet isn’t the only medium for phishing. With the rise of smartphone popularity, the use of SMS messages and phone calls to mobile numbers with requests for information has also risen. It is possible for an attacker to change the caller ID to present false information or to even use a VoIP phone number with an area code local to the potential victim.
They can then claim to be a bank, their credit card processor or even local law enforcement. As they are in the business of scamming people, no claim is too outrageous, so long as it works.
How to avoid getting hooked
First, don’t panic. No matter what that email, phone call or website says, it is never that bad. If it were, you would not be receiving notice of it via pre-recorded message in a phone call, email or from a pop-up ad while online.
When Wells Fargo sees suspicious activity on your account, their normal policy is to decline the suspicious transaction and to have their fraud prevention team give you a call, over the phone, to find out if it is a legitimate purchase.
PayPal does occasionally freeze accounts when there are problems, but they will never send you an attachment to fill out and return to them. They will also never ask you for details like your mother’s maiden name, except maybe as a secret question for when you forget your password.
The FBI does have a reputation for shutting down illegal websites and replacing their home page with a warning page of their own. However, visiting one of those sites is not an illegal activity, so you cannot be fined for visiting a website.
If the email does contain a link, it will be to their main home page or maybe to a login page. To check the link, simply place your mouse arrow over the link, but do not click on it. When your mouse arrow “hovers” over a link a small pop-up appears at the bottom of the window showing where that link goes.
Just because you see PayPal in blue letters with an underline in the body of the email, it doesn’t mean that the website that will open will be PayPal’s. It could be “Bob’s Famous Rip Offs and Scams, Inc.”
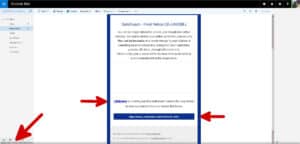
On mobile devices, while reading the email you can press and hold a link inside the email to see where it goes. You will then have the option of copying the URL, opening it in your device’s default browser or to cancel the selection.

Sometimes, the URL will be obfuscated using sites like bit.ly. Sites like this are meant for shortening URLs for fitting into tweets or micro-blog posts where you have a limited amount of characters for your post. There is no reason to hide the destination URL for a legitimate correspondence delivered via email.
For fraudulent websites, the main things to check are the actual site address, the existence of a security certificate and the validity of any such certificate.
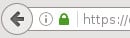
The green padlock icon in the above example shows that the URL displayed in the address bar matches the URL that is embedded in the security certificate and that the security certificate comes from a reputable certificate issuer. You can read more on how to recognize secure websites here.
In the case of emails specifically, it helps to learn how to check the email header details, especially on any email that calls for immediate action. Even the stuff from your boss should be double checked, just to be on the safe side. You would be amazed at how easy it is for a phisher to “spoof” an email address that belongs to someone you know and trust. This is more of a spear phishing attack, but is still rather easy to pull off.
If the email contains a link that looks legitimate, you will still want to avoid clicking on it or opening any attachments. Large companies like PayPal and major banks do not send emails with attachments. Instead, any important documents are either sent via snail mail or are attached to your online account. Their emails will simply let you know that there is a message for you and encourage you to log into your account to find out what that message contains.
Also, take note of who the email is addressed to. If it is legitimately from your bank or anyone that you actually have an account with, it will be addressed to you. Not to “Dear Valued Customer” or “Dear Sir or Madam” or even “Dear Account Holder”.
While it is true that there have been massive data leaks of accounts, most phishers and scammers don’t bother with purchasing these databases. They rely on more outdated methods because, the sad fact of the matter is, they still work.
The exception to this is in the case of spear phishing. Those emails will be addressed to you because the spear phisher has targeted you specifically. Don’t get too paranoid over this. They are probably monitoring several hundred people just waiting for them to post something, somewhere that can be used as bait.
Even if they only get a return of one percent, that’s still hundreds of identities or even credit cards stolen that can now be sold on the dark web, used to open lines of credit, run up outrageous charges on existing lines of credit or even just target them for other scams like the now infamous Nigerian 419.
A Summary of Red Flags/Danger Signs
- One of the biggest red flags that can indicate a possible phishing attack is a misspelled word or bad grammar. All of the entities that these scammers mimic employ professional writers and editors to make sure that their correspondence and web presence is free of typos and is grammatically correct. If you can spot an error, the odds are very good that the email did not come from the company that it claims to be from or that the website does not actually represent the company listed. If you can’t spot any typos or grammatical errors, it does not necessarily mean that the info can be trusted.
- Any company that has you in their database will also address any emails directly to you and not to a generic or vague recipient. If you have a PayPal account, any email that you receive from PayPal will begin with a greeting containing your name. If it says “Dear Sir or Madam”, “Dear PayPal account holder” or even “To whom it may concern” then you can be sure that it did not come from PayPal. Again, in the case of spear phishing, just because it has your name in the salutation, it doesn’t mean it’s legitimate.
- If the email has an attachment delete it and move on to other things. Banks, PayPal and the FBI all know better than to include an attachment on any official correspondence. Do not open it, do not reply to the email and most definitely do not click on any links in the email. It is a scam and can be safely trashed. The only exceptions to this rule is digital signatures, which can sometimes show up as attachments. Apart from that, attachments are to be treated as the unholiest of unholies.
- Email headers are a record of where an email came from, where they were sent to and what address to use for replies. There is a lot more information stored in the header, but these three are the important ones for identifying a potential scam. It is actually very easy to make an email look like it came from PayPal or Bank of America, but it is a lot harder to hide the actual email address that it came from. In Hotmail, when an email has been flagged by Microsoft as junk, the full email address of the sender is automatically displayed at the top of the email when opened. If the email has not been flagged as junk, then you can check the email address by opening the email and placing your mouse arrow over the name of the sender.
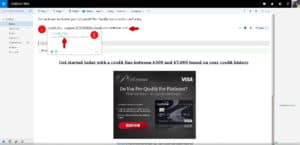 A small box will pop-up containing the full email address of the sender. If it is actually from the company that it claims to be from, you should see the company name after the ‘@’ symbol.
A small box will pop-up containing the full email address of the sender. If it is actually from the company that it claims to be from, you should see the company name after the ‘@’ symbol. - The same applies to any links inside an email. If you place your mouse arrow over the link, but don’t click on it, you will see a small line at the bottom of your browser window with the destination URL of the link. If that URL does not contain the name of the company that the email claims to be from, do not click on it. Close that email, open your web browser and type in the company’s web address yourself.
- Any claim that you have money coming to you from anyone outside of your home country is almost 100 percent guaranteed to be fraudulent. Nobody is paid to go through old files to find recipients of money. No banker or government official of any kind will try to get money out of their country by contacting a random individual over the internet and striking up a deal. No bank that you’ve never dealt with will have an account in your name just waiting for you to take possession of.
- A website claiming to have found viruses on your computer. There are no websites that have the ability to scan your computer for viruses. Computer viruses are insidious little things that require much greater access to your computer then a mere webpage can manage. A real anti-virus program not only looks through the files on your hard drive for signs of infection, but it also searches through running programs, active services, hidden utilities and any other area where these bugs are suspected of lurking about. To check all of these areas takes time and resources like processing power. Not something that can be done from a website.
- A pop up from the FBI is fining you for illegal activity online. The FBI doesn’t use popups to fine criminals online. They will shut down sites that traffic in illegal goods or are engaged in piracy, but they cannot fine people for visiting such sites. Only a judge has the authority to issue a fine against a suspected criminal. The FBI can gather evidence, build a case, seek a warrant for the arrest of a suspect and conduct the actual arrest when a warrant has been signed by a judge. They do not have the authority to levy fines against anyone.
- A site you visit regularly pops up and prompts for a login but does not display the green padlock is highly suspicious. A legitimate company login will have a security certificate that matches the URL of the site which can be verified by your browser displaying the green padlock icon mentioned earlier. Your safest bet for these pages is to close the page, open a new tab and type in the actual URL yourself. Alternatively you can go through your list of favorites or bookmarks and click on the link that you have saved there.
- Spoofed sub-domains. This is a clever tactic where the scammer sets up a website that looks exactly like the homepage of the company or agency that they wish to impersonate. Unfortunately, the URL for that entity is already taken. For example, they cannot currently register the domain name paypal.com because PayPal already has that domain locked up. But, let’s assume that the phisher-to-be already has iamascammer.com registered as his own personal domain. He can then try to register the sub-domain of paypal.iamascammer.com. They then create a webpage for that sub-domain that looks exactly like PayPal’s, but with an added twist. Whenever a user types in their login information they are presented with a page that asks them to confirm their identity. The scammer can literally ask for whatever information he wants and enough people will fall for the trick to justify the effort. After they’ve entered their information, the spoofed site then redirects to PayPal’s actual site providing the user’s login information and they are none the wiser, but will probably get a bit poorer as soon as the scammer cleans out their PayPal account.
Where to report phishing emails
Most people who receive phishing emails will simply delete them, and that’s fine. But if one slips through your spam filter and seems particularly effective or dangerous, or if you’re just fed up and want to take a more proactive role in stopping phishing, you can report phishing emails to the authorities.
In the US, you have a few places to report phishing. Forward the email to:
- the FTC at spam@uce.gov
- the Anti-Phishing Working Group at reportphishing@antiphishing.org
- the United States Computer Emergency Readiness Team (US CERT) at phishing-report@us-cert.gov
- and the impersonated entity, be it a bank or some other company
The FTC notes that it’s helpful to include the full email header, which includes the display names and email addresses of both the sender and recipient, the date, and the subject. Some of this info is hidden by default on some email clients, so you may need to search how to display this info.
UK residents can report phishing scams on the Action Fraud website. Users just need to answer a few questions about the phishing attempt and who it impersonated to get the appropriate email address to forward it to.
Repairing the damage after being hooked
If you have been hooked by some clever phishing, then you need to do some damage control. Start by treating this as a case of identity theft, mainly because that’s what it can lead to if you don’t act.
Shutdown your computer immediately just in case there was a ransomware package included with the phishing attack. If you think a ransomware infection is likely, get some professional help. If the PC is a work computer, let your IT team know immediately. Do not hesitate on this one. An infection of this type can spread quickly to the company servers and network data stores causing real havoc.
If it’s a personal computer you’re still going to need help. Ask your work IT team if they can help. Odds are that they may not, but ask anyway. If they can’t help, they may know someone in your area that can, like a local freelancer or contractor. The goal here is to get the assistance of someone who can either restore your important data or protect what hasn’t been locked up yet.
Your second action needs to be just as immediate. You need to get online, using a different computer, and start changing your passwords. Start with your online banking and go through all of the sites that have anything to do with your finances. Once your finances are safe, move on to your email accounts, file storage services, social media accounts and any other sites that require a login. If you can’t remember all of the sites that require a login, do not turn your computer back on to check, not until it has been gone over by a competent technician.
You will also want to contact the major credit agencies and put a fraud alert on your credit account as a potential victim of identity theft. This does not stop an identity thief from making use of your identity, but it does make it easier to clean up the damage to your credit after the fact. You will also want to start monitoring your credit very closely over the next few years. The faster you react to a case of identity theft, the easier it is to regain control of your identity when things go wrong.
If you gave out your debit or credit card information, call your bank and report that card as stolen. You will also want to carefully monitor the account that the card was attached to. If the account number itself was given to the attacker then have your bank close that account and open a new one, transferring your funds to the new account in the process. Keep a close eye on your account statements watching out for suspicious or unauthorized purchases.
If your PayPal or eBay login is at risk, try to login to your account. If you are able to, change your password and all of the security questions. Setting up two factor authentication is highly recommended for any accounts that allow it, as it helps reduce the risk of an attacker being able to hijack your account, even if they have the login credentials.
If you are no longer able to login to your account then you need to contact the company and report an account hijacking immediately. The longer you wait to act on this, the more damage can be done to your accounts.
Statistics
The problem of phishing and online scams has gotten so bad that several companies are currently employed to gather and report the facts relating to these types of attacks. According to a recent report approximately 30 percent of phishing emails get opened. This is considered a conservative estimate based on one company’s sampling of data. There are others who claim this number can be as high as 50 percent, but lack the hard numbers to back up their claim. In another report, there was a large increase of phishing emails being sent out in 2016.
JPMorgan Chase ran a test in 2015 to see how many of their employees would be taken in by a phishing scam. A whopping 20 percent opened the phishing email. That’s quite an impressive success rate. More than enough to justify the crafting of a single email and pumping it through a bulk email program to a list of hundreds of thousands of email addresses.
The Anti Phishing Working Group identified 123,555 unique phishing websites at the beginning of 2016. In the last quarter of 2016 they reported 95,555 unique phishing email campaigns were received just by their customers. That report also finds that companies in the financial services sector were the preferred targets 19.6 percent of the time in these campaigns.
It doesn’t take much math to come to the realization that a major banking entity like JPMorgan can potentially fall victim to just under 4,000 of those campaigns. That’s potentially a little under 4,000 successful phishing campaigns in just one bank.
Summary
The main rule concerning emails is to take them all with a grain of salt. If your bank really needs to lock your account, they will call you on the phone. When PayPal has a problem with your account activity, they notify you, but do not ask for any more information than they already have. And they most certainly will never ask you to confirm your account details in an attachment that you need to fill out and send back to them.
Most institutions have strict policies against sending any email attachments. Also, any email coming from the actual entity will be addressed to you, will contain your name or account username, and will have a reply-to address that is part of that entity’s actual web presence.
When it comes to websites, be wary of any sites that pop up in a new browser window or tab. Especially if you’re browsing through sites containing images of bunnies with pancakes on their heads.
Anybody can setup a website to look exactly like another site. They can even get a certificate issued that shows that the URL is what it claims to be. But if the site is https://www.barikofamerica.com/ then you can be sure that it is not actually affiliated with Bank of America, even though it might look exactly like their home page.
Please note that at the time of this writing, https://www.barikofamerica.com/ is not an actual website. It is used here merely as one way to use a misspelling to disguise a potential phishing site.
While writing this piece I got an email from a Mr. Robert Pridemore with the National Security Agency in New York. The sender claims that he was sent to Nigeria by the Federal Government and that he was handed a file with a red cross on it, signifying that my money has not been transferred.
The sender’s email address shows up as “megasize@mega.bw”, the physical mailing address provided in the email turns out to be for Chase Bank in Oakland Gardens, NY, and the phone number has a San Fernando Valley, CA area code. Finally, this supposedly official representative of the NSA provided a gmail email address for me to contact him directly. He or she did not even make an attempt at disguising the email address via a bogus “mailto:” link.
Sadly, this is the minimum level of sophistication needed for a phishing campaign to work. While I would never contact Mr. Pridemore, too many people out there do and end up getting soaked for hundreds if not thousands of dollars each or have their identity stolen and sold off to much more unscrupulous characters.
What sort of things have you seen that seemed either too good to be true or were just way to suspicious? Leave a comment below and share your example of a phishing attack.